Sex, Secret and God: A Brief History of Bad Passwords
Kyle Rankin
Chief Security Officer
Purism
Linux Journal Tech Editor, Columnist
For Your Consideration

Agenda
- Introduction
- RMS and the MIT Password Revolt
- Golden Age of Computer Passwords
- Dotcom Boom Password Policies
- XKCD and the Password Renaissance
- We Will RockYou: Modern Cracking
- New Password Approaches
- 2FA
- Password Reset Attacks
- Conclusion
- Questions?
Introduction
- Want to hack an account? Guess the password
- Weakest link in security for decades
- Easy to blame user, but not user's fault
- Largely IT/Security industry's fault
- Focus on theoretical attacks, ignoring real users
- Decades of bad password advice, policy
- This talk:
- How did we get here?
- What are the current threats against passwords?
- What can we do today?
RMS and the MIT Password Revolt
- Computers didn't always have passwords
- Passwords weren't always viewed as a good thing
- Richard Stallman viewed passwords as a means of control
- Most people don't know RMS is a password cracker
- RMS joined MIT AI lab in 1971
- The system they built didn't have passwords.
RMS and the MIT Password Revolt
RMS and the MIT Password Revolt
Golden Age of Computer Passwords
- In the beginning, computer passwords like traditional passwords
- Many computers didn't support passwords longer than 8 characters
- Some computers ignored case (password = PASSWORD)
- Result: passwords single words, simple, easy to guess
- People tended to all pick the same passwords.
Golden Age of Computer Passwords

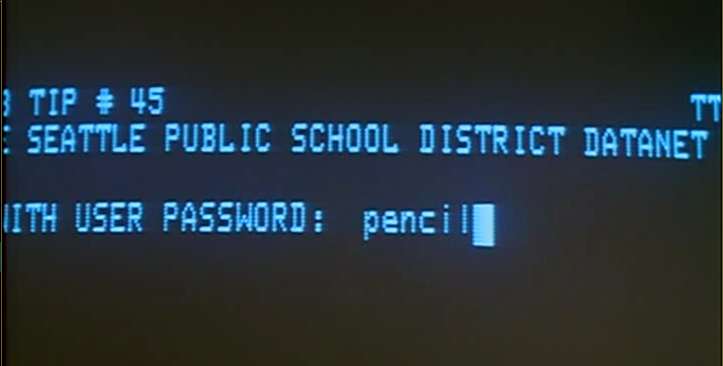
- Popular passwords were things like: "love" "sex" "secret" (and "god")
- And of course "password"
- To hack someone, just try all dictionary words
- If that's too slow, you guess words important to them
- Spouse names, children, pets, sports teams
- Main way people got hacked in movies.
Golden Age of Computer Passwords
Golden Age of Computer Passwords
Golden Age of Computer Passwords
Dotcom Boom Password Policies
- Tools like John the Ripper automated password cracking
- As computers got faster, so did dictionary attacks
- IT depts started responding with password policies
- Centralized Windows admin tools made enforcement easy
- Password policies well-meaning, but misguided
- Users generally hated them.
Dotcom Boom Password Policies
Minimum Password Length
- Policy: "Passwords must be at least 6 characters"
- Reason: Makes dictionary attacks take longer
- Theoretical Combinations: 1-300 million combinations
- Users Picked: "qwerty" "secret" "password" "123456"
- Attackers: Removed shorter words from dictionary.
Dotcom Boom Password Policies
Password Complexity
- Policy: "Passwords must contain at least one upper case letter"
- Reason: Increases total # of password combinations, removes passwords of pure numbers
- Theoretical Combinations: 19 billion
- Users Picked: "Qwerty" "Secret" "Password"
- Attackers: upper-cased first letters in dictionary words.
Dotcom Boom Password Policies
Password Complexity
- Policy: "Passwords must contain at least one upper case letter and one number"
- Reason: Increases total # of password combinations
- Theoretical Combinations: 57 billion
- Users Picked: "Qwerty1" "Secret1" "Password1"
- Attackers: Added 0-9 to the end of dictionary words.
Dotcom Boom Password Policies
Password Complexity
- Policy: "Passwords must contain at least one upper case letter and two numbers"
- Reason: Stop users from just adding a number to the end
- Theoretical Combinations: 57 billion
- Users Picked: "Qwerty84" "Secret69" "Password11"
- Attackers: Added two digits to end of dictionary words
- Attackers: Added significant two-digit date to end of password guesses.
Dotcom Boom Password Policies
Password Complexity
- Policy: "Passwords must contain at least one upper, one number, one symbol"
- Reason: Add order of magnitude to entropy, stop users from just adding numbers to the end
- Theoretical Combinations: 782 billion
- Users Picked: "Qwerty84!" "Secret69!" "Password11!"
- Attackers: Added a few symbols to the very end of dictionary words.
Dotcom Boom Password Policies
1337 5P34K
- Complex passwords can be hard to remember
- IT people invented clever way to build complex passwords
- Dictionary word + leet speak!
- "password" becomes "P455w0rd"
- Or if you need symbols: "P@55w0rd!"
- (This was an actual admin password at a prior job)
- Turns out attackers know leet speak too.
Dotcom Boom Password Policies
Password Rotation
- Policy: "Passwords must be changed every 3 months"
- Reason: Limit time to crack before password changes
- Reason: Limit time hacker has on system after compromise
- Users Picked: "Password1!" then "Password2!" then "Password3!"
- Attackers: Guessed weak password, learned your scheme, put in back door within hours of hack.
Dotcom Boom Password Policies
Policy Problems
- Draconian password policies bad for everyone but hackers
- Wastes IT time troubleshooting account lockouts
- Frustrates users who pick a "hard" password that gets rejected
- More complex the password, more painful to rotate
- Often leads to passwords on post-it notes
- Encourages users to pick weakest possible password that meets standard
- Passwords end up being based on a dictionary word + transformations
- Hackers still able to guess majority of "complex" passwords.
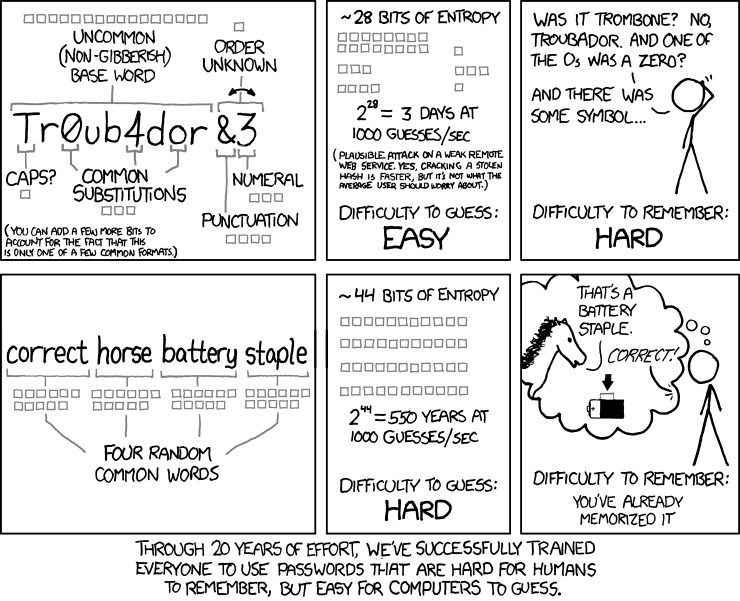
XKCD and the Password Renaissance
XKCD and the Password Renaissance
- Focus shifted away from complex passwords toward long passphrases
- My personal corporate password policy: 12-char minimum, no rotation, no complexity
- Theoretical Combinations: 95 quadrillion
- 8-char mixed case, numbers, symbols = 7.2 quadrillion
- No rotation encourages much longer, complex passwords
- Passphrase could be a long movie quote or song lyric
- Or use Diceware to generate random multi-word passphrase with dice
- Muscle memory takes over pretty quickly.
XKCD and the Password Renaissance
- Don't have to take my word for it
- New NIST guidelines discourage password rotation, complex passwords, encourage passphrases
- "Verifiers SHOULD NOT impose other composition rules (e.g., mixtures of different character types) on memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically)"
- Print this out, take this back to your IT dept.
We Will RockYou: Modern Cracking
- Modern password cracking very advanced, uses sophisticated tools
- Actual sporting event at DEF CON
- Most password cracking starts with a hashed password database dump
- Allows crackers to brute force hashes offline
- Tools like hashcat support variety of hashing algorithms, use huge dictionaries
- Supports transformation patterns to apply to each dictionary word (leet speak, capital first letter, numbers at the end, etc.)
- Dramatically reduces the number of guesses needed to crack "complex" passwords
- oclhashcat can use GPU for acceleration
- In 2012, my $280 Radeon 6950 = 350,000 MD5 comparisons per second.
We Will RockYou: Modern Cracking
The RockYou Hack
- Most users reuse passwords across sites
- When hackers crack a password on one site, attempt that username/password across other popular sites
- If can get access to an email account, trigger password resets for remaining user accounts
- In 2009, RockYou company was hacked, exposed 32 million user accounts
- All passwords stored in plain text
- Treasure trove of popular passwords to try elsewhere
- Immediately added to everyone's dictionaries.
We Will RockYou: Modern Cracking
Advanced Cracking
New Password Approaches
- What's a good password? One you can't remember
- Very long (20+ char), truly random, complex
- Use new password for each account
- Hard to remember, so use a password manager
- KeePassX Open Source, encrypts pw db, includes handy pw generator
- Some passwords must be memorable
- Password strength depends on threat
- Average: 12 char+ passphrase, no complexity
- Advanced: 5-6 word diceware, or passphrase not on Internet
- Speak multiple languages? Mix and match!
2FA
- Main categories of auth: something you know/have/are
- Passwords = something you know
- Best insurance against pw cracking is Two Factor Auth (2FA)
- In addition to pw must provide additional factor from different category
- Something you have (keys, token, phone), something you are (biometrics)
- Once attacker guesses pw, has to also compromise your 2FA device
- Most 2FA implementations use form of something you have.
2FA
- SMS: Send txt message with random multi-digit code
- Weakest choice, attackers starting to intercept SMS, better than nothing
- Push notifications sent to phone
- Convenient, but security depends on phone + strength of app
- TOTP: Generate multi-digit code that rotates every 30 seconds
- More secure approach, uses shared secret between server and hardware token or software
- U2F: Use key inside hardware token to respond to challenge from server
- Simple, very secure, not widely supported (yet).
Password Reset Attacks
- Password not always the weakest link
- Sometimes easier to attack account via pw reset
- Gain access to user's email, trigger pw reset on account you want
- 2FA helps, but attackers can socially engineer orgs to disable it
- Facebook offering Delegated Account Recovery as an option
- Uses your FB account instead of email as trusted source for resets
- New protocol, still in closed beta.
Conclusion
- Strong authentication is possible today
- Infosec can't agree on what it looks like
- We still repeat the mistakes that led to bad password policy
- Attackers have learned from real users from the beginning
- Time for defenders to do the same
- Researchers must shift focus from hacker movies to real-world users
- IT should resist checkbox security, question "best practices"
- Requires better security education across the board
- Stop blaming users.
Questions?
Additional Resources